Quick Cookie Notification This site uses cookies, including for analytics, personalization, and advertising purposes. The following changes were made to this article: Microsoft has updated this bulletin to more clearly enumerate the ports over which RPC services can be invoked and to make sure that customers who choose to implement a workaround before installing the patch have the information that they must have to protect their systems. RPC provides an inter-process communication mechanism that allows a program that is running on one computer to seamlessly run code on a remote computer. You should also block any other specifically configured RPC port on the remote machine. The attacker would be able to take any action on the system, including installing programs, viewing changing or deleting data, or creating new accounts with full privileges. Description Your system may require one or more security patches or hotfixes from Microsoft. 
| Uploader: | Samutaxe |
| Date Added: | 27 July 2018 |
| File Size: | 55.98 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 34589 |
| Price: | Free* [*Free Regsitration Required] |

Customers who have already installed the patch are protected from attempts to exploit this vulnerability and do not have to take further action. Technical Update September 10, New Zealand - English. For more information about this vulnerability, visit the following Microsoft Web site: Tell us what we can do to improve the article Submit. Advanced vulnerability management analytics and reporting. To exploit this vulnerability, an attacker would have to send a specially formed request to the remote computer on specific RPC ports.
View Cookie Policy for full details.
MS03-026: Buffer Overrun In RPC Interface Could Allow Code Execution (823980)
Skip to main content. Updated the "Security Patch Replacement Information" sections to indicate that this patch has been replaced by MS The attacker would be able to take any action on the system, including installing programs, viewing changing or deleting data, or creating new accounts with full privileges.
For more information about the security patch MSclick the following article number to view the article in the Microsoft Knowledge Base: Your system may require one or more security patches or hotfixes securty Microsoft.
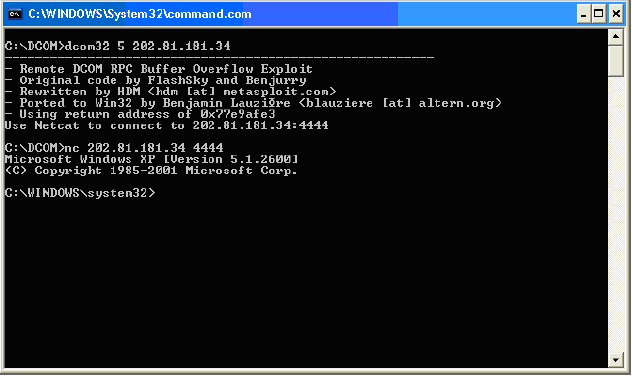
RPC provides an inter-process communication mechanism that allows a program running on one computer to seamlessly execute code on a remote micrpsoft. Download the package now.
Crna Gora - Srpski. In addition, the bulletin has also been updated to include information about Windows Service Pack 2 support for this patch. Although Microsoft urges all customers to buletin the security patch at the earliest possible opportunity, there are several workarounds that you can use in the interim to help prevent the vector that is used to exploit this vulnerability.
However, the "mitigating factors" and "workarounds" discussions in the original security bulletin did not clearly identify all the ports by which the vulnerability could potentially be exploited. The patch was and still is effective in eliminating the security vulnerability.
Blocking these ports at the firewall will help prevent systems behind that firewall from being attacked by attempts to exploit these vulnerabilities. Back to Search MS This site uses cookies, including for analytics, personalization, and advertising buloetin.
MS () Scanning Tool Available - Windows Setup, Administration & Security
The patch was and still is effective in eliminating the security vulnerability. The failure results because of incorrect handling of malformed messages. You should also block any other specifically configured RPC port on the remote machine.
South Africa - English. Bosna i Hercegovina - Hrvatski. United Kingdom - English. Mitigating Factors To exploit this vulnerability, the attacker must be able to send a specially crafted request to portportportor any other specifically configured RPC port on the remote computer.
Search - Threat Encyclopedia - Trend Micro NZ
These workarounds are temporary measures. If these ports are not blocked, or in an intranet environment, the attacker does not have to have any additional privileges. This interface handles DCOM object activation requests that are sent by client machines to the server. Ms03026 Cookie Notification This site uses cookies, including for analytics, personalization, and advertising purposes.
The following sections provide information that you can use to help protect your computer from attack.

Комментарии
Отправить комментарий